Resource Profile:
De4dot 是一款功能强大的开源 .Net 反混淆工具,广泛应用于对 Dotfuscator、.Net Reactor 等处理后的程序进行解密和还原。该工具以命令行操作为主,非常适合软件开发者和逆向工程爱好者使用,是技术人员工具库中的重要成员。
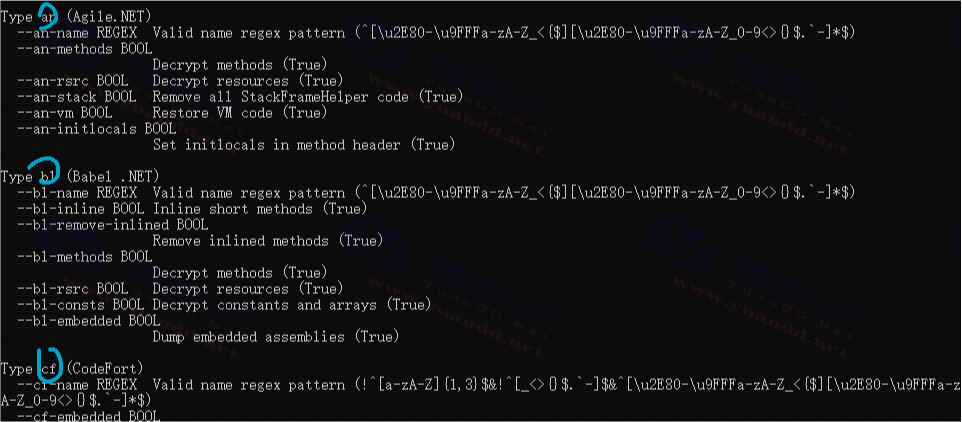
支持的反编译工具包括:
Agile.NET (CliSecure)、Babel.NET、CodeFort、CodeVeil、CodeWall、CryptoObfuscator、DeepSea Obfuscator、Dotfuscator、.NET Reactor、Eazfuscator.NET、Goliath.NET、ILProtector、MaxtoCode、MPRESS、Rummage、Skater.NET、SmartAssembly、Spices.Net、Xenocode
操作指南:
1. 打开命令行窗口:
- 进入 De4dot 所在的文件夹,按住 Shift 键并右击鼠标,从弹出的菜单中选择“在此处打开命令窗口”。
- 或者直接打开命令提示符后,使用
cd命令定位到 De4dot 的安装目录。
2. 执行反混淆命令:
在命令行输入以下格式的指令:
de4dot <目标文件路径>例如:
de4dot D:\NetworkHelper.dll执行成功后,工具将在目标目录生成一个后缀为“-cleaned”的反混淆文件。例如:NetworkHelper-cleaned.dll
3. 验证反混淆结果:
使用 .NET Reflector 或其他反编译工具打开生成的反混淆文件(如 NetworkHelper-cleaned.dll)。通过查看文件中的源代码定义的变量和方法,确认反混淆是否成功完成。
工具优势:
De4dot 不仅支持多种主流的 .Net 混淆工具,还能高效地完成解密任务,是逆向工程与调试的理想选择。
Photo Gallery:
Installation and usage instructions:
A detailed installation and configuration tutorial is included in the zip!
- Can free downloads or VIP member-only resources be commercialized directly?
- The resources on this site are collected and organized through the network, for personal research and study purposes only. The copyright belongs to the legal owner of the software and program code, users should verify the copyright and legality of the resources, prohibited for commercial use, illegal activities or any violation of national laws and regulations.
- Disclaimer of liability for program or code bugs, compatibility issues or functional defects, etc.
- As the resources on this site are collected and organized through the network, not the site's original, it can not fully guarantee its functionality or code compatibility. Users need to verify whether the resources meet the needs of their own, due to the following circumstances lead to losses, this site does not assume any responsibility:
Programs, source code and other computer software resources may contain code vulnerabilities (bugs), compatibility issues or functional defects left by the developer. This site does not provide free repair services for such technical defects, users need to bear the risk of debugging, modification or abandonment of the use.