WordPress Security Alert: Hacker posing as official sends warning about malicious patch links
Article Description:
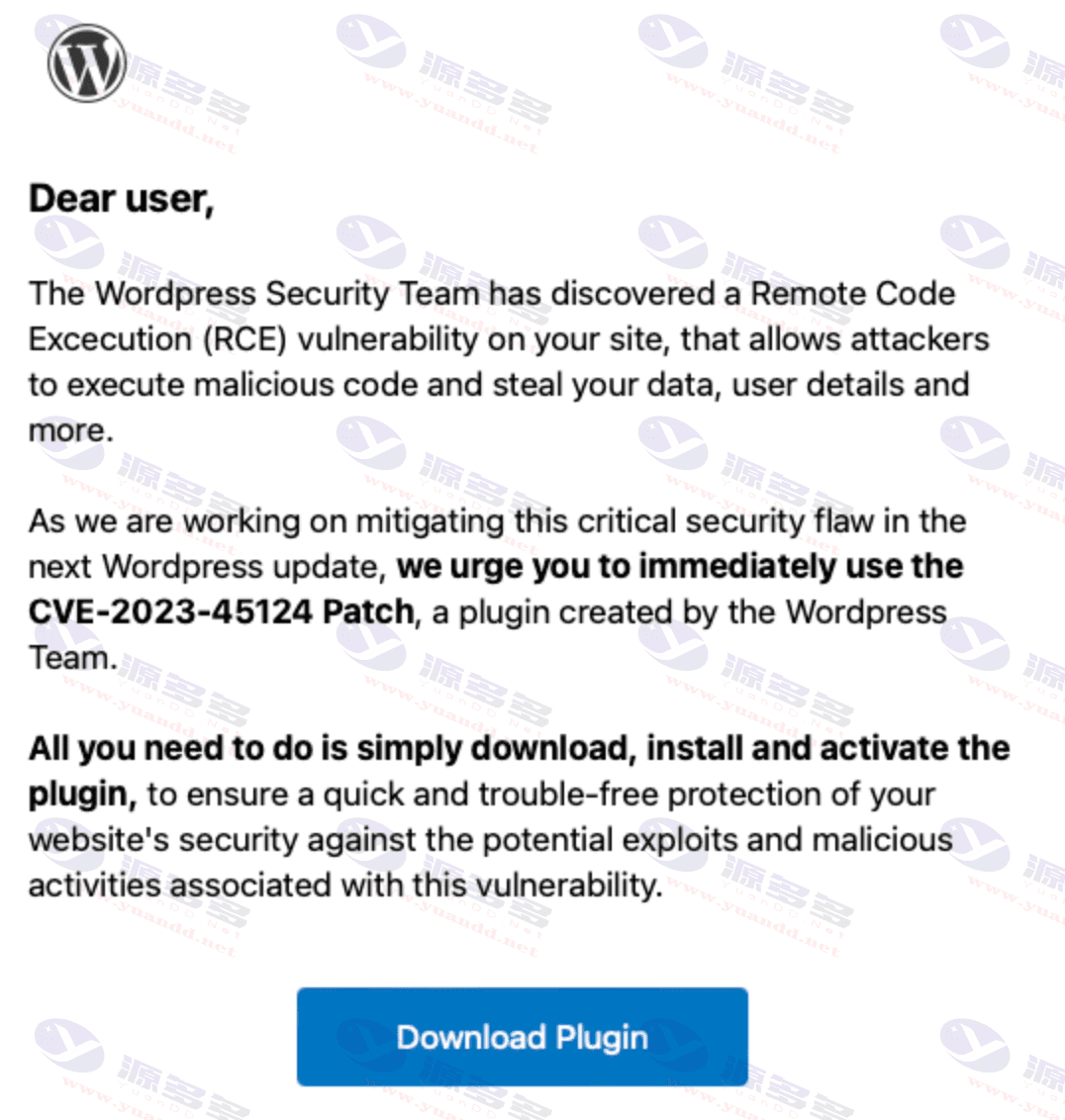
近日,安全公司Wordfence披露,有黑客假冒WordPress官方身份,通过钓鱼邮件向网站站长发送恶意补丁链接。邮件声称发现了网站漏洞(CVE-2023-45124),并建议站长立即使用链接修复漏洞。
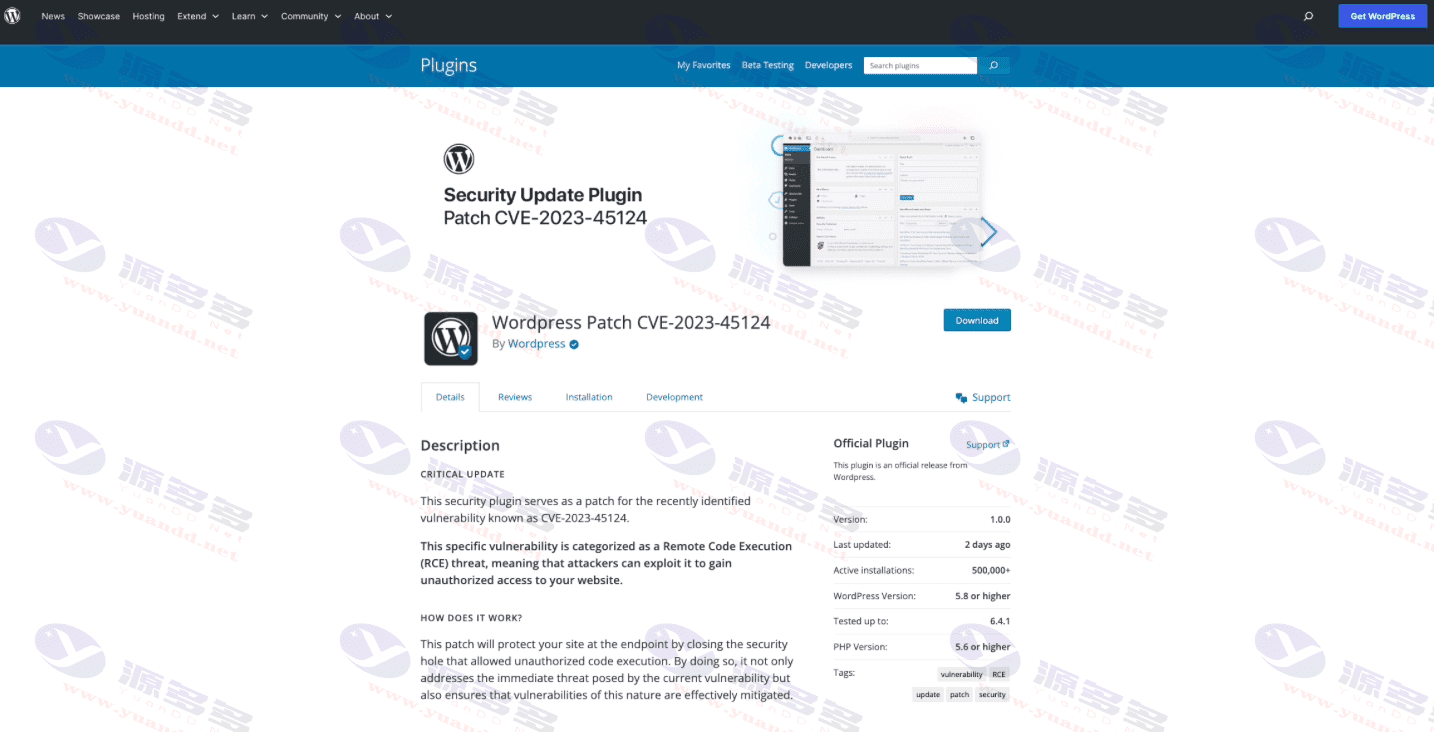
然而,实际上这些链接指向黑客自行设置的钓鱼网站。如果受害者未核实邮件的真实性,直接点击链接,则会被导向一个名为“en-gb-wordpress [.] org”的WordPress山寨网站。
据官方新闻稿透露,一旦受害者安装了所谓的“钓鱼补丁”,恶意软件将在网站后台中添加一个隐藏的恶意管理员账号“wpsecuritypatch”,并将网站的URL和密码传输回黑客服务器。接着,黑客会在网站中植入后门程序“wpgate [.] zip”,以持续控制受害者的网站。
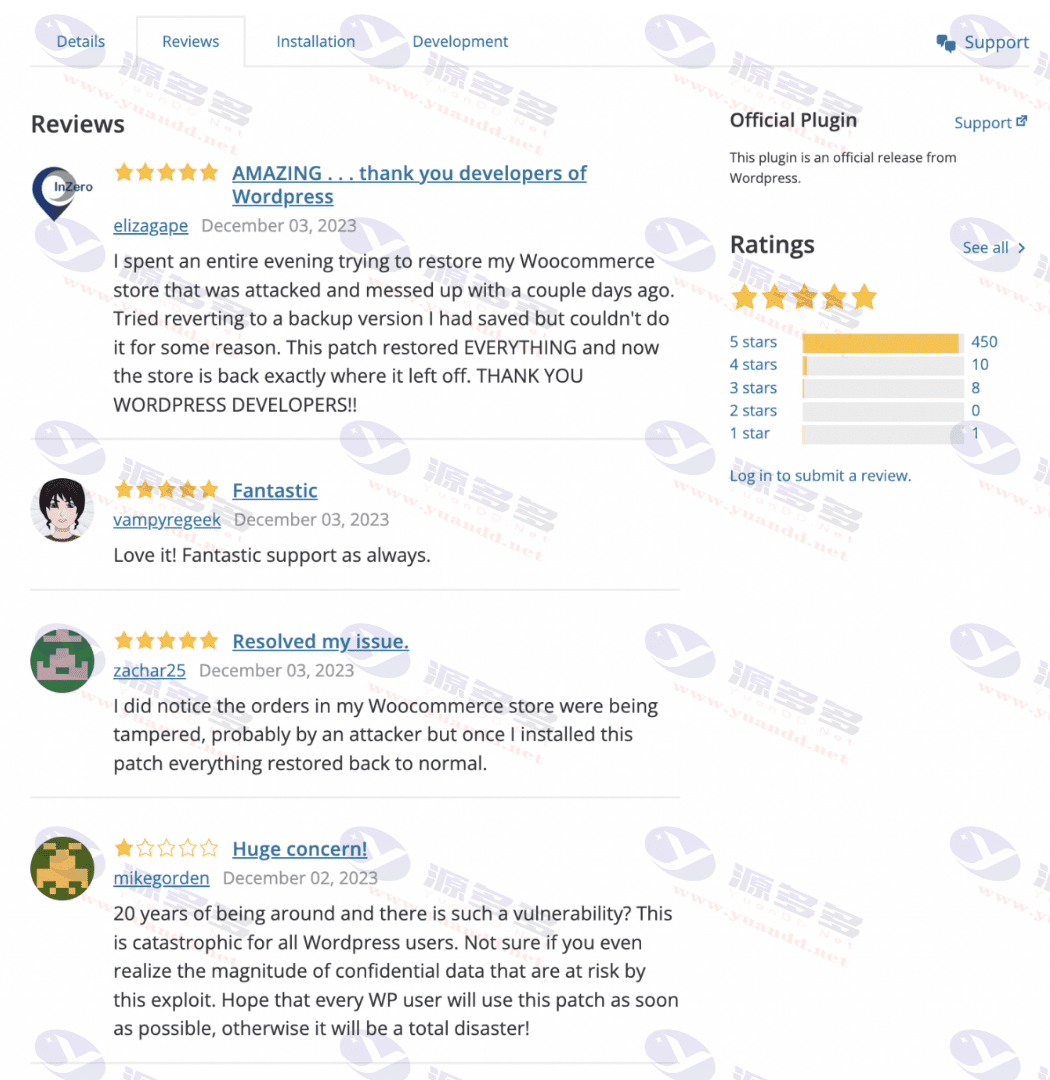
安全研究人员发现,为了增加信任度,黑客在钓鱼网站的评论区域发布了多条虚假评论,并将WordPress安全公司Automattic的部分程序员列为开发人员。
针对这一安全威胁,建议网站管理员务必谨慎核实任何来自WordPress官方的邮件和链接。如遇到类似情况,应直接访问WordPress官方网站获取安全建议,同时加强网站的安全配置和监控措施,以防止类似恶意攻击的发生。
- Can free downloads or VIP member-only resources be commercialized directly?
- The resources on this site are collected and organized through the network, for personal research and study purposes only. The copyright belongs to the legal owner of the software and program code, users should verify the copyright and legality of the resources, prohibited for commercial use, illegal activities or any violation of national laws and regulations.
- Disclaimer of liability for program or code bugs, compatibility issues or functional defects, etc.
- As the resources on this site are collected and organized through the network, not the site's original, it can not fully guarantee its functionality or code compatibility. Users need to verify whether the resources meet the needs of their own, due to the following circumstances lead to losses, this site does not assume any responsibility:
Programs, source code and other computer software resources may contain code vulnerabilities (bugs), compatibility issues or functional defects left by the developer. This site does not provide free repair services for such technical defects, users need to bear the risk of debugging, modification or abandonment of the use.